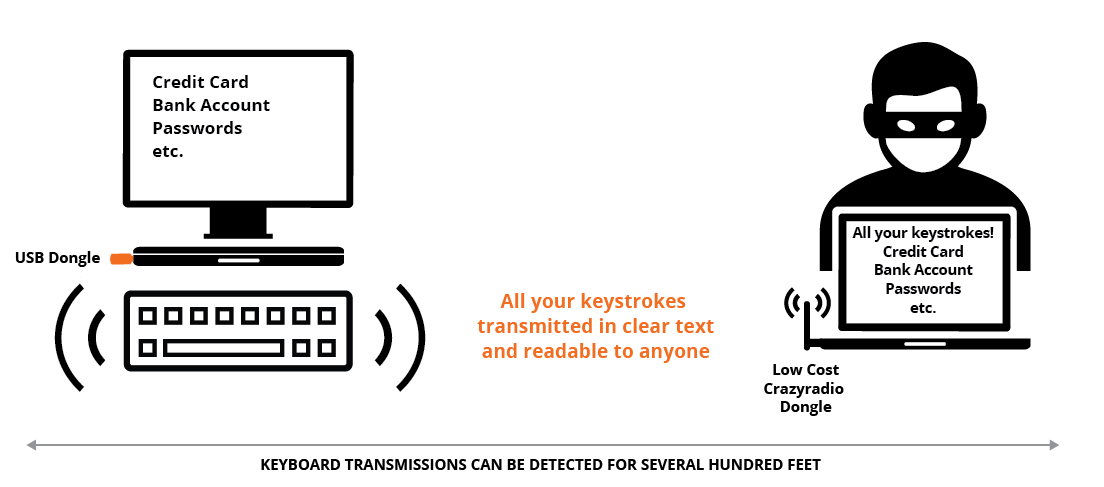
KeySniffer is a set of security vulnerabilities affecting non-Bluetooth wireless keyboards from eight vendors. The wireless keyboards susceptible to KeySniffer use unencrypted radio communication, enabling an attacker up to several hundred feet away to eavesdrop and record all the keystrokes typed by the victim. This means an attacker can see personal and private data such as credit card numbers, usernames, passwords, security question answers and other sensitive or private information all in clear text. The equipment needed to do the attack costs less than $100 putting it in reach of many teenage hackers.
The keyboard manufacturers affected by KeySniffer include: Anker, EagleTec, General Electric, Hewlett-Packard, Insignia, Kensington, Radio Shack and Toshiba.
Take Action
Learn to Protect Your Privacy
KeySniffer allows anyone to view your private information as you type it into your wireless keyboard. To be alerted as and when Bastille Networks finds new vulnerabilities sign up for Bastille Research Alerts at the bottom of this page.
KeySniffer exposes personally identifiable information such as:
Card Numbers, expiration date, CVV code
Bank account usernames and passwords
Answers to security questions: Name of your first pet, mother’s maiden name, etc.
Network access passwords
Any secrets: business or personal typed into a document or email
Date of birth
Employer confidential information
““When we purchase a wireless keyboard we reasonably expect that the manufacturer has designed and built security into the core of the product. Unfortunately, we tested keyboards from 12 manufacturers and were disappointed to find that eight manufacturers (two-thirds) were susceptible to the KeySniffer hack.” ”
How does KeySniffer work?
KeySniffer is a set of security vulnerabilities affecting non-Bluetooth wireless keyboards from eight vendors. The wireless keyboards susceptible to KeySniffer use unencrypted radio communication protocols, enabling an attacker to eavesdrop on all the keystrokes typed by the victim from several hundred feet away using less than $100 of equipment. This means an attacker can see personal and private data such as credit card numbers, usernames, passwords, security question answers and other sensitive or private information all in clear text. Read more.